Title: Getting Started on the Novena
Date: 2016-12-15 22:44
Category: Novena
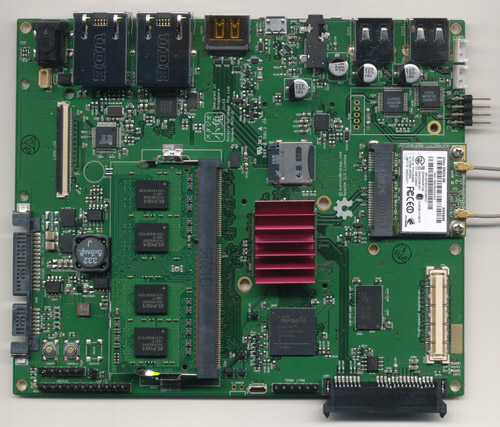
Novena is an open hardware and F/OSS-friendly computing platform. It is a small single-board Linux PC, with a Freescale i.MX6 (ARM
Cortex-A9) CPU and a Xilinx Spartan-6 LX45 FPGA.
It is available in limited quantities through crowd supply.
The Novena PVT-2 requires some initial setup. You will need to attach a USB keyboard and HDMI monitor.
Once this is done, most of us prefer to run it headless, and ssh in.
You may also want to bring the packages up to date:
$ sudo apt-get update
$ sudo apt-get upgrade

The avalanche noise board is a Novena daughter board that contains a zener-diode noise circuit that can be read directly by the FPGA.
(More information from FT: block diagram, schematics, ...)
It is available in limited quantities directly from Fredrik Thulin, and will be distributed at the PrahaWorkshop.
Cryptech maintains an apt repository, with two binary packages for the Novena:
- a bitstream, to be configured into the FPGA
- software, to run on the CPU
All commands are run on the Novena.
- First, get the hactrn CA certificate:
$ wget http://www.hactrn.net/cacert.asc
Get the key used to sign the CA certificate.
$ gpg --recv-keys 2DC6FF82
Validate the CA certificate
Install the CA certficiate.
$ sudo mkdir /usr/share/ca-certificates/hactrn.org
$ sudo mv cacert /usr/share/ca-certificates/hactrn.org/cacert.crt
$ sudo dpkg-reconfigure ca-certificates
- Get the repository key.
$ wget https://apt.cryptech.is/novena/apt-gpg-key.asc
Validate the key.
$ id=37A8E93F5D7E7B9A
$ gpg --recv-key $id
$ gpg --check-sig $id
$ gpg --export $id | sudo apt-key add -
See the apt-key(8) manual page for more information about the APT key database, including how to remove keys you don't want anymore.
Install the key.
$ sudo apt-key add apt-gpg-key.asc
- Get the packages
Configure apt to use the repository.
$ sudo wget -q -O /etc/apt/sources.list.d/novena.list http://apt.cryptech.is/novena/sources.list
Update the package index file.
Get the cryptech meta-package.
$ sudo apt-get install cryptech-novena
This installs the cryptech-novena-rtl and cryptech-novena-sw packages.
The cryptech-novena-rtl package includes an init.d script that configures the FPGA on system startup. This script should run automatically as part of the install process.
Once you've performed the steps above you should be able to upgrade to newer
version of the code using the normal APT upgrade process, eg:
$ sudo apt-get update
$ sudo apt-get upgrade
The PKCS11 token is in /usr/lib/libpkcs11.so. In order to start using it you need to set a pin and an SO pin. This you do with p11util thus:
(echo 12345678;echo 1234) | sudo p11util --set-so-pin --set-user-pin --pin-from-stdin
It is strongly suggested to change the so pin and pin (in that order above) to something sensible. Now your token is ready to use. Your favorite PKCS11-client may or may not work depending on the state of support for PKCS11 function calls - please open tickets for whatever is missing. If you want/need to talk PKCS11 from another host, you could install and configure PKCS11Proxy on both the novena and your host. Note that currently pkcs11-proxy doesn't handle differing word-lengths so your client-side will have to be 32bit (since the novena is).
The lab DNSSEC signer MUST, at this point, be running on a 32-bit system in order to work with the 32-bit Novena.
https://www.dropbox.com/s/f8b4s9vic7hsqyb/cryptech-proxy-lab-20150718r2.pdf


